550 5.1.8 Access denied, bad outbound sender
Microsoft disables accounts from sending outbound messages when the email account hits an undisclosed threshold. “We monitor accounts that are sending spam, and when they exceed an undisclosed limit, the account is blocked from sending email. There are different thresholds for individual users and the entire tenant” – Microsoft 365 EOP
A Non-Delivery Report (NDR), also referred to as a ‘bounce report’, with the NDR Error Code: “550 5.1.8 Access denied, bad outbound sender AS(42004)” is typically generated by Microsoft if one or more of the following conditions is met:
- Your account is compromised (or appears to be).
- You hit daily, hourly, or recipient sending service limit.
- Microsoft thinks you’re sending spam base on their outbound policies and the spam confidence.
- Spam complaints from email recipients.
The bounce report is very vague and looks like this:
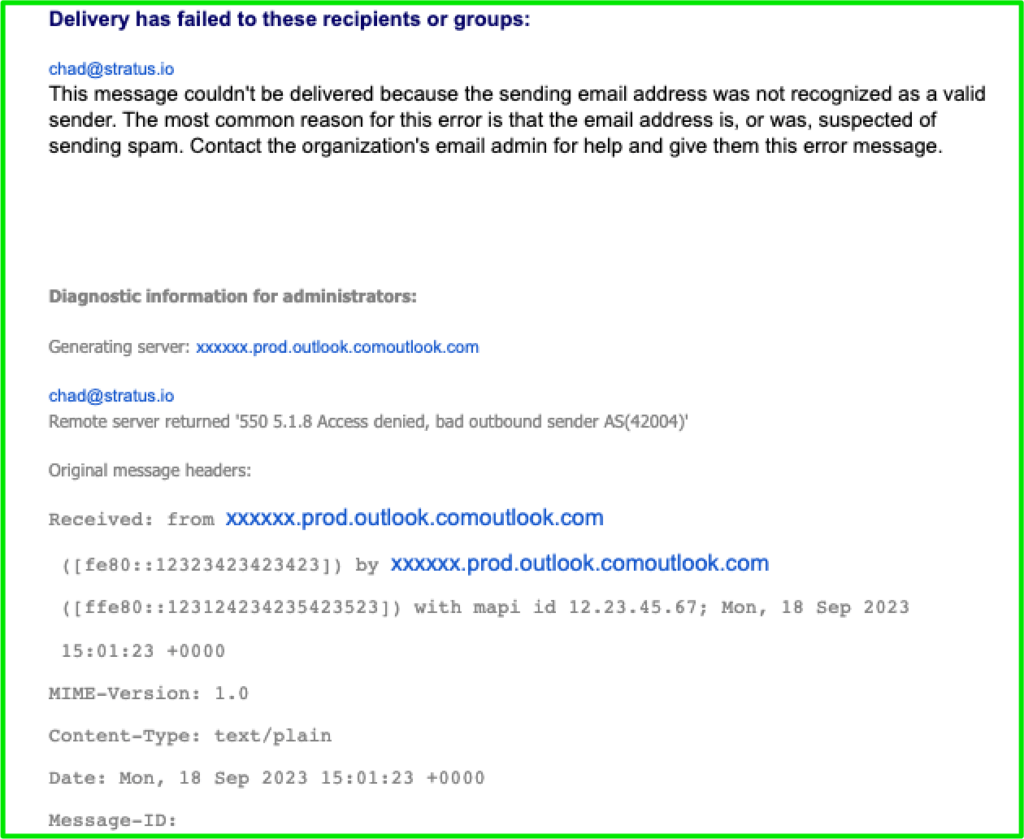
Delivery has failed to these recipients or groups:
recipient@domain.com
Your message couldn’t be delivered because you weren’t recognized as a valid sender. The most common reason for this is that your email address is suspected of sending spam and it’s no longer allowed to send email. Contact your email admin for assistance.
If you are the email sender and the admin, keep reading this post which helps troubleshoot unblocking a 550 5.1.8 ACCESS DENIED error. If you’re not the email admin please copy the URL for this article and contact your email admin for assistance. (ps – Google Workspace has a similar NDR 69585 Bounce Error.)
Note – If your NDR says Remote Server returned ‘550;5.7.711 Access denied, bad inbound connector. AS(2204)’, then your organization may be unintentionally blocking the Replyify connector.
How to Fix a 550 5.1.8 Access denied, bad outbound sender Report
Microsoft provides different account configurations and support depending if on your Office 365 Business Basic, Standard or Enterprise license. More information about removing blocked users from the restricted entities page here.
- Confirm that the email account has not been hacked then proceed to Step 2
- Reviewing account activity for suspicious login access.
- Consider enabling multi-factor authentication (MFA) and/or resetting passwords.
- The Admin can go directly to Restricted Users Page to remove blocked users or follow the navigation below while logged into the Microsoft Admin 365 Defender Portal:
- Select Email & Collaboration > Policies & Rules > Threat Policies > Tenant Allow/Block Lists. Next, find and select the blocked email account > click Unblock.
- Alternatively, navigate to Email & Collaboration > Review > Restricted User > Unblock
- If your Office 365 account was purchased via third party, like GoDaddy, you’ll need to follow their instructions to submit a request to unblock.
- More information can be found on security presets here.
- Create an optional Alert Policy to to verify and configure the alert for user restricted from sending.
- Follow the steps to remove restrictions and wait 1 hour to send emails
How to Edit Anti-spam outbound policy (Default)
If you followed the steps above and there were not any users listed in the Defender Portal, the 550 5.1.8 report may be caused by the user surpassing the company’s volume based limits.
It’s possible to increase your email sending limits, but maxing out email volume may cause even more issues with blacklists and domain reputation. Suspected spam is automatically routed through Microsoft’s high-risk delivery pool.
Pro Tip: Consider setting up an alternative email address for sending cold emails. If you’re already using a new domain (or subdomain), confirm that it’s been added as an accepted domain in the admin center.
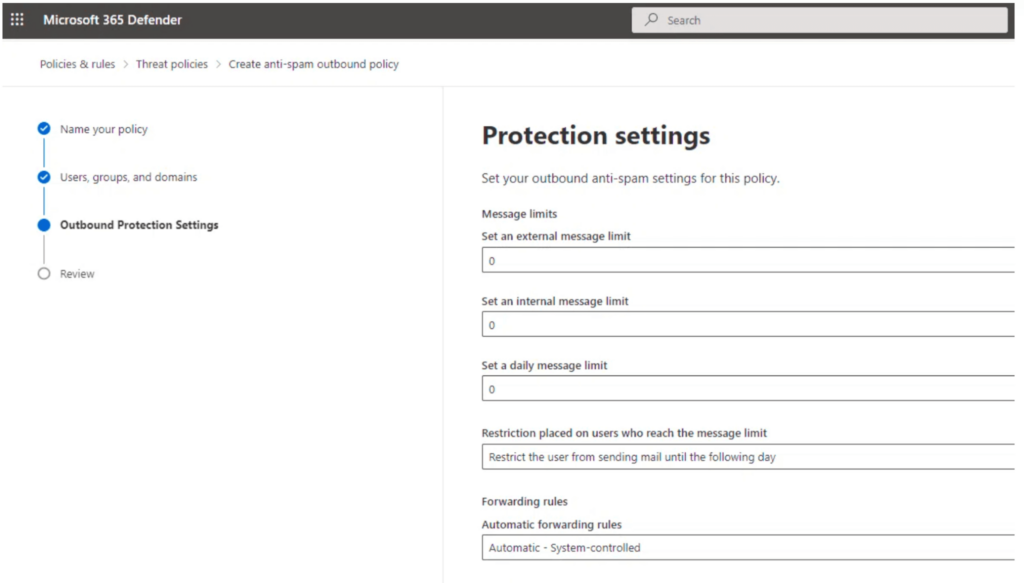
You can follow the steps below to increase your anti-spam outbound email volume limits:
- Log into your admin account and navigate to the Anti-Spam Policies page
- Select the ‘Anti-spam outbound policy’
- Scroll down the page and click ‘edit protection settings’
- Increase the volume limits for external messages
- Wait up to 24 hours before sending bulk email
Pro Tip: your spam policy limit for outgoing emails is the most common self-inflicted reason why internal emails are blocked.
Microsoft Thinks I’m Sending Spam
Microsoft 365 comes packed with features like Exchange Online Protection (EOP) which serves as the control center for email admins to create policies for malware, spam and more. The Defender Portal must be logged into separately from your Office 365 Admin Portal. Read more about anti-spam protection here.
The 550 5.1.8 ACCESS DENIED report should contain information about why the email(s) triggered the error. Once you’ve confirmed the email account is NOT hacked and addressed the email volume, it’s time to dig deeper to adjust your EOP settings.
- Create and configure your custom outbound anti-spam policies in EOP
- Click the + button and select Outbound from the dropdown
- Name your policy > add users, groups or domains > configure protection settings
- Set up notifications to automatically send a bcc copy of the suspicious outbound emails to the admin for review
Fortunately Microsoft has a much more robust set of docs for managing the outbound bulk emailing for your 365 account.
Read our post about Microsoft’s anti-spam policies for more information.
If you’ve completed the 3 phase review above and you’re still running into deliverability issues, make sure the email senders are following best practices for email deliverability. Persistent deliverability issues may signal that it’s time to consider setting up a new domain for cold email.
